DotXWe love to help people with their technology! Archives
August 2023
Categories |
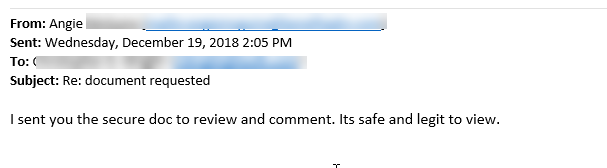
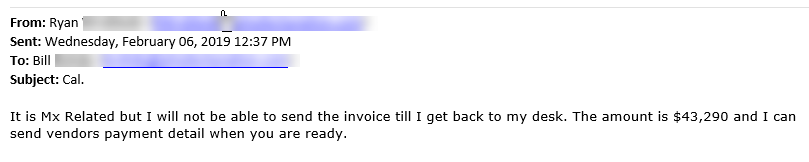
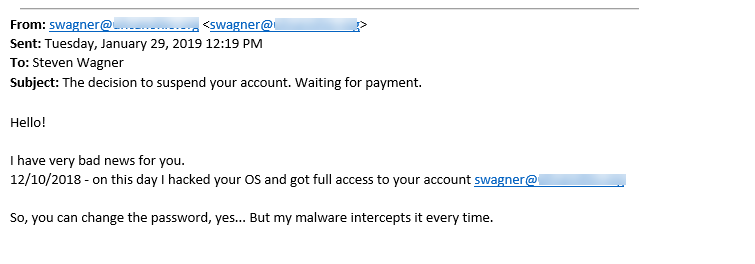
5/30/2019 What is Email Phishing and Spoofing?We use email every day. We use our email addresses for work, keeping in touch with family and friends, coupons, newsletters, we even receive some of our bills via email. We trust that the emails we receive are valid, but it is this trust that has made it easier for hackers to take advantage of us. There are many ways hackers can use email to try to get your personal information. While it is easy to fall prey to these scams – it is equally easy to avoid them and protect yourself with just a few precautions Email Phishing is when you receive an email asking you to provide information. Sometimes this email may even appear as though it came from someone you know. These emails may include a link asking you to click on it or an attachment. There is always a call to action for you the receiver. Some examples they may use can be: - Your package is delayed – click here for tracking information. - Your email is hacked – click here to reset your password - I have pictures of you (doing something you shouldn’t be) – click here (or email / text here) - Your bank transaction is pending – click here to confirm details - I need you to pick up some gift cards for me Any attachments may claim to be an invoice or order information. The example below included an attachment. It looked like it came from a known contact of the receiver. The fact that there is no greeting, the language is awkward, and that it goes out of its way to say that it is “safe and legit” are all red flags on this one! As a rule – never click on links or open any attachments that you are not 100% sure are legitimate. Open a web browser and go to the website directly or create a new email chain to the sender asking them to verify the legitimacy of the attachment or request. Also – it is always a bad idea to send gift card info or financial information, complete with pin numbers through email! If you receive an email like this – please forward it to [email protected] – in most cases there is nothing we can do, other than confirm that it is a phishing attempt. But it is important for us to be aware so we can take extra precautions. Email Spoofing is when the fraudulent email appears to come from a known contact. They’ve disguised their real email so that when you receive it – it looks as though it came from a reputable source. Most often, these spoofed emails are also phishing emails. We are able to assess these emails and review the email header to see the real sender information – even if it is not visible to you the receiver. The picture below shows an example of this. Once again – if you receive an email that you suspect is coming from a spoofed email – forward it to [email protected] as soon as possible. Generally, there is no other action required, but it is important for us to keep an eye on it. It also can’t hurt to make the spoofed sender aware that they may have been spoofed. They can then follow up with their IT provider to ensure their email is secure. Email Fraud can encompass the examples above or can be when an email account is hijacked and used by a person with malicious intent. There are many ways to take advantage of email users, but these are the most common. This can be especially disarming when the suspect email comes from your own email address! The below email is an example of this, but luckily the recipient knew something seemed fishy and dug a little deeper. In this instance, the hacker probably used brute force to actually gain access to the user’s email. We know this because when we hover our mouse over the email link, it is actually the correct sender’s email. The content of this one is what alerts us to the fact that it is fraud. These are the most dangerous kinds of email fraud because they indicate that the email may have been hacked. You (or the affected sender) may need to change the email password immediately. Contact [email protected] for help with this. We may not be able to undo damage already done, but we can certainly stop the attack and keep an eye on things to ensure there are no lingering issues. What to do:
If you do not receive confirmation from us that a ticket has been opened –
please call: 614-239-7677 Option 1 (during business hours) Option 3 (outside of business hours)
0 Comments
Leave a Reply. |

 RSS Feed
RSS Feed